Most orders for IN STOCK items placed by 12PM CST M-F ship SAME DAY. Orders for custom items and prints may take additional time to process.
Sometimes you need to be able to prove to your ISP that the issue is on their end. Sometimes you need to prove to yourself that the issue on your end. Sometimes there are hardware or software problems with your router that can be mitigated by putting a device between them (such as the one where pfSense won’t reestablish WAN link after it fails). The great thing about having a switch between the ONT and the router is that it make it incredibly easy to mirror the ONT’s port and put a sniffer such as WireShark on the line to listen to packets in the wild.
This can be an incredibly effective way of seeing just what data is passing between the ISP and your network. It’s also a great way to make sure your firewall or internal network is operating correctly. You may think your ISP is at fault only to learn your proxy server (think Squid) is acting up.
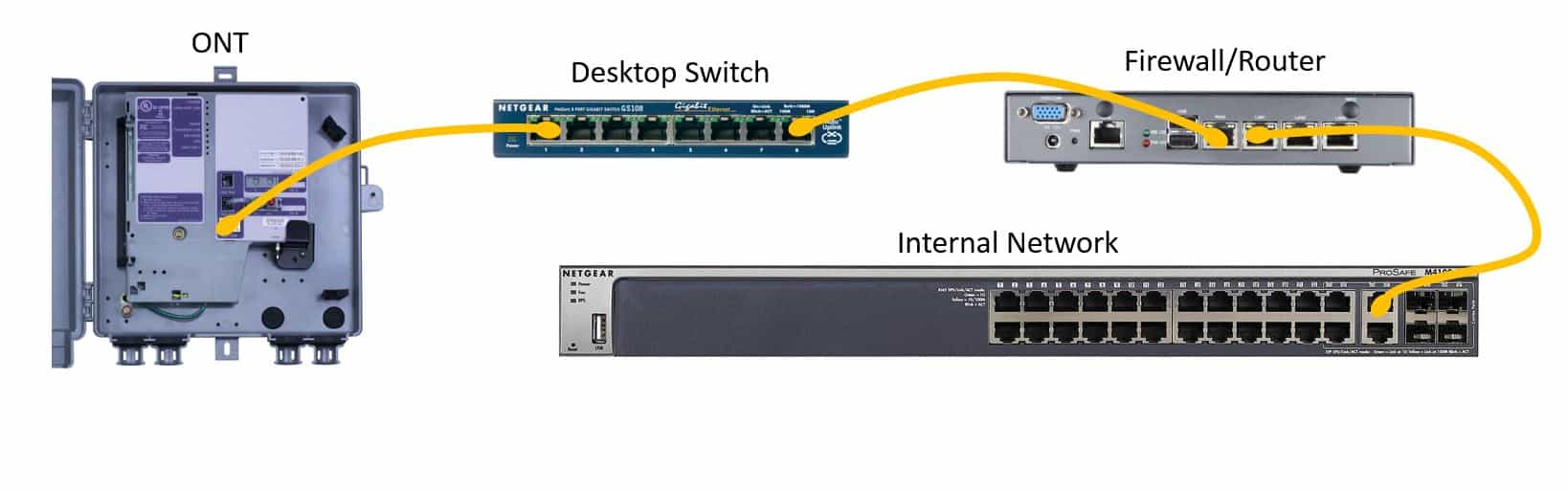
The obvious choice might be just to place a desktop switch between the ONT and the router. This option does work. This will give you the ability to keep the WAN link on your router up and all times, even if the ONT fails. For some hardware or software incompatibilities where you just don’t want the router to be aware the WAN link is down physically (such as the router is on UPS and the ONT is not. This is a great solution. However, it will not give you the ability to mirror a port for traffic sniffing. These desktop class switches are also made with cheaper components which might impact performance, and they are more prone to failure.
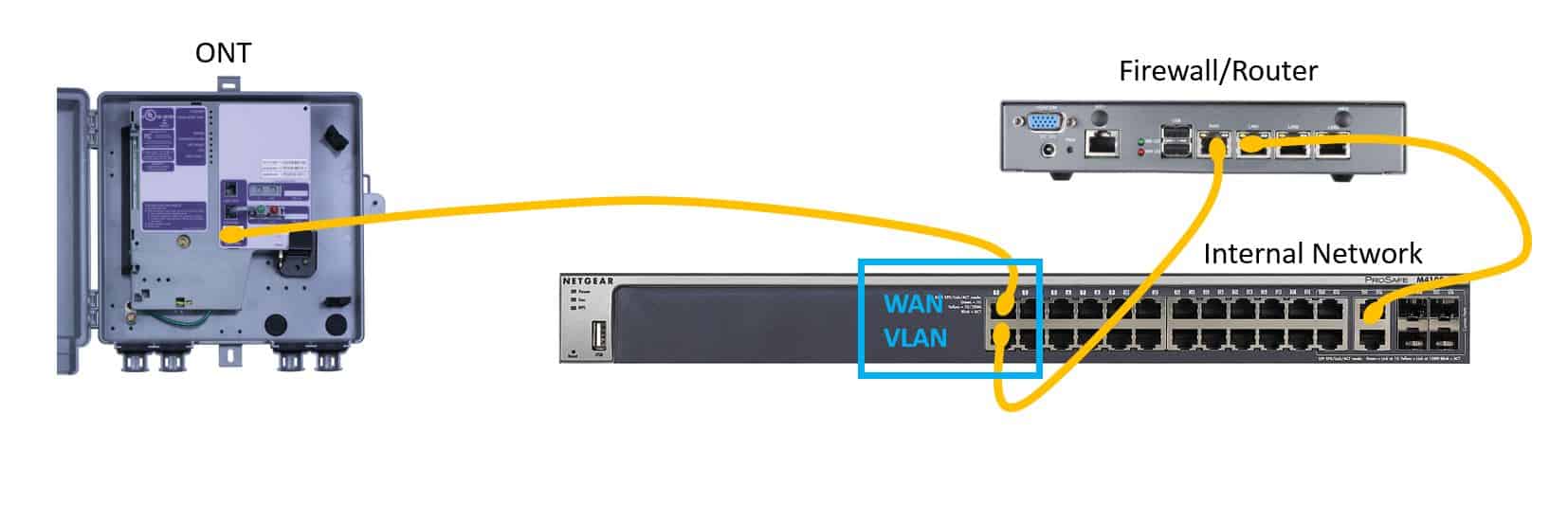
Option 2 is the better, more robust solution, but it does require a VLAN capable switch and a little understanding of more complex networking scenarios. This option creates a Virtual LAN on two ports on a managed switch. Plug the ONT into one port and the WAN interface of the router into the other port. This gives you the option to mirror either port to a third port on the switch allowing you to sniff traffic outside the firewall. If you have two routers in a CARP (failover) configuration you’d just add a 3rd port to this VLAN and connect both routers. This would allow for failover in the case of a router failure. Your ISP (Frontier FioS in my case) would not be aware that there is more than one router connected, because the devices share a virtual MAC address and the IP address that your ISP handed you via DHCP.
In this configuration it is critically important to make sure that there is no intra-VLAN traffic, as that could allow an attacker to bypass your firewall! These need to be untagged, completely segregated VLANs.
There are few additional benefits of having a switch between the ONT and the router. Depending on how much you value your privacy and how far you want to take things:
So there you have it. I currently run option 2 in my network using the WAN VLAN. This works extremely well and is the one I would recommend.
Some of you might be asking if you can plug more than one router into the ONT this way. Unless you’re using a CARP setup, or unless you have business account with multiple static IP addresses the answer is unfortunately no. Your ISP will not issue additional IP addresses to your network beyond the first one. All additional DHCP requests will be dropped.
If you like our content maybe consider upgrading to Premium. You’ll get access to
23 Responses
Mike, thank you so much for this article! I dug for hours on DSL reports unable to find any information on this. This is greatness!
Thanks for being a fan Sandy!
Oh my god. Thank you for such a simple explanation of how this works. I’ve been wanting to do this for a while and all my tech buddies kept telling me it wouldn’t work. I suspected that Verizon/Frontier would have no way of detecting such a setup. Thanks!!!
This sounds very interesting to me. I have purchased a VLAN capible router (mini PC to host pfsense) and a VLAN capable switch. I kinda get it and I certainly understand your proviso: “… it is critically important to make sure that there is no intra-VLAN traffic…”. Is there any elaboration for a VLAN initiiate to make sure we get this right? Even perhaps a link to an existing, pedestrian how-to. Thx for setting the seed!
Not really. Just make sure the only VLAN communicating on those ports is the WAN VLAN ID. Also, make the PVID of the ports the same VLAN ID.
Mr Muray – I think I understand the VLAN / PVID statements. What about the switch IP parameters? What IP/Mask would one use on the switch? DLink DGS-1100-05. – gar
The switch will not have an IP address on the WAN VLAN, only on the LAN VLAN.
Hi Mike. I have an additional advantage for the switch in the middle; actually I put a switch at the ONT end and the other end of the connecting Ethernet cable connects to my home’s core switch. The advantage here is that I have Ethernet devices near my ONT in the garage that need connectivity (cameras etc) and I don’t want to have to run another Ethernet cable. I just use a different native VLAN to connect to the ONT as the other ports with inside devices on them and then just tag all the VLAN through the single “FIOS pulled” Ethernet cable. On the other end, I obviously have access to each of the VLANs as I need to handle them as the DMZ router and any internal devices. I get the same benefits that you describe in your article and also have no need for additional cable pulls for my cameras, but maintain L2 separation of the networks. More so, I don’t even have to port mirror, I can now just Mirror a VLAN and I can see or stat the ONT to Router traffic; kind of useful when sniffing to try figuring out how to handle the MOCA cable boxes without UPNP support in a Cisco router vs. the Actiontec supplied by FIOS :).
Good note: With the switch method and your thought of switching routers, you can use the same MAC address for the two routers WAN side and same IP subnet as well as set BIA to MAC of Actiontec LAN side and easily swap between the two to compare sniffing traces without having to restart settop boxes as the ARP table still matches.
However, I still physically shut or unplug one of the routers when doing this so there is no MAC conflict on my switching infrastructure.. But as you said, the switch keeps link up at the ONT so it never goes down either.
-Guy
Hi, I found your article interesting and hope you can shine some further light on my current plight. I recently started working at a company where they have FiOS for business and 2 pfSense firewalls on VMWare. I have been tasked with setting up new Netgate 5100 pfSense appliances to replace the old firewalls. I noticed that the secondary (original) firewall never showed an active link to the WAN (FiOS) ever. This is still the case even after I set up the new appliances correctly. I have been reading online that Verizon has to do something on their end to allow multiple WAN devices to be recognized by the ONT. Any thoughts/advice/links on if that’s the cause and/or where I can go to get this all resolved?
If you’ve setup failover correctly, the pfSense boxes will share a MAC address. FiOS will never have a clue there are two WAN devices in the first place. And since its the middle man switch that will link them physically on Layer 1 there will only be one Ethernet cable to the ONT.
ONT–> Port 1 on WAN switch/VLAN
pfSense primary box –> Port 2 on WAN switch/VLAN
pfSense failover box –> Port 3 on WAN switch/VLAN
Mike, have you had success with Option 1 when the service from VZ is residential class with single dynamic IP?
Yes. I don’t have business class service.
Mike, This sounds great as I have been dealing with FiOS support for the past few days and am ready to pull my hair out. My setup had always been my own enterprise gateway as the main device connected to the ONT and the FiOS router behind it on a separate subnet from the rest of my computers. It had internet access but an internal IP from my gateway. I just upgraded my service to the new TV One and in order to get it to function I had to make the FiOS router the first device connected to the ONT. I obviously tried inserting a switch between the ONT and the router so I could also connect my gateway and although both got Public IPs from VZ only the last device to get the IP was able to connect to the Internet. So I am wondering in your Option 2 where you talk about a failover router but then say that wouldn’t work to connect more than one router to the ONT, I am curious as to why? To me this sounds great. If there is something else I would need to do to get this Option 2 to work please clue me in as I really want my equipment to handle traffic for my computers.
Thanks
5
4.5
Hello Mike. I was trying to set up scenario 2 on my home. I set a separated VLAN for ports connecting to my router and ONT, however my router cannot obtain I address lease from the ISP. My ISP required vlan tagging for internet (VID: 12). Do you think that is the cause of the problem here?
Once upon a time i have positive sure that i already implemented something similar on my house with success but for some reason i reverted.
Thanks and regards
Gonçalo
Mike,
Having alot of issues getting this to work, based on your instructions. I am hoping you will see this and be able to respond. I have setup vlan 99 with two ports, one for the ONT connection and one for the connection from my OPNsense firewall. Both ports are untagged. In this config I never get the DHCP IP from Verizon. Any thoughts?
Thanks,
Steve
Hello Steve,
Did you ever find out a solution? Cause I’m on the same step as you, I bring back this theme to my home network. Our ISP’s do vlan tagging for internet…
Thanks in advance,
Regards
Hi Mike. I attempted Option 1 and I am having some issues. It may also be important to note that I have a computer wired into the desktop switch as well as the router. Several times each day, I am disconnected from the internet. At that point, I must either unplug the router’s power cable and plug it back in, or unplug and replug the ethernet cable. Upon doing that, the connection is restored, but it is annoying to do several times every day. I lose my connection on my computer that is wired into the desktop switch as well when this happens. I was hoping you may know of a solution. Thank you
Aaah, I think I understand what I did wrong when I was tinkering with this last weekend, after reading this. I had my ports tagged on the vlan used in the PPPoE settings (vlan 6). But they need to be untagged.
I’ll schedule some more downtime next weekend. 🙂
I just hang up on a Verizon rep that could not believe that I wanted your 2nd setup. I want to segregate totally what belongs to work and what belongs to home. “No intra-VLAN traffic”. That the left hand knows nothing of what the right hand does … They want to sell you what is easy and convenient for them. I don’t need a high density switch for your setup. Any recommendations on 8 to 16 ports managed switches that won’t brake the bank?
You don’t need to talk to Verizon to do this.
in 2023, seven years later I cannot believe that this solution worked but it did. Thank you very much Mike. What is the logic behind this working when replacing ONT and everything else did not. Thanks again.